LINE CTF 2024 - hacklolo
목차
0x00. Introduction
C++로 만들어진 바이너리로 분석하는데에 상당히 까다로웠다.
Structure
;
;
C++에서 basic_string 객체가 가지는 특성 때문인지 문자열을 그냥 저장하지 않고 id를 예를 들면 다음과 같이 저장한다.
id_ptr: 문자열이 저장된 주소id_size: 문자열의 길이id[8]: 길이 8까지의 문자열은 여기에 저장하고 더 긴 문자열은 다른 영역을 할당받아 저장id_end: 쓰이지 않는 영역으로 chunk 관련 데이터로 추정
0x01. Vulnerability
Improper Check
__int64 __fastcall
used_db에는 총 32개의 user를 저장할 수 있는 공간이 있는데 login_790E()에서 user를 확인하는 범위는 33개이다. 때문에 user_list[32] 이후 영역이 또 하나의 user로 인식되며 다음과 같이 영역이 겹쳐진다.
after user_list | user |
|---|---|
| user *user_list_ptr | char *pw_ptr |
| _QWORD count | _QWORD pw_size |
| _QWORD login_try | char pw[8] |
| _QWORD is_login | _QWORD end_pw |
| char *welcome_ptr | char *id_ptr |
| _QWORD welcome_size | _QWORD id_size |
| char welcome[8] | char id[8] |
| _QWORD canary | _QWORD end_id |
| user *current_user | char *email_ptr |
| _QWORD login_success | _QWORD email_size |
| char *jwt_key | char email[8] |
| _QWORD jwt_key_size | _QWORD end_email |
| _QWORD jwt_key_end |
따라서 바이너리 실행 시 출력되는 "Welcome!"이 id인 계정으로 로그인이 가능하다.
JWT Counterfeit
join시 생성되는 coupon은 HS256으로 생성한 JWT 값으로, siganture 부분은 HMAC-SHA256을 이용해 생성된다. 이 때 출력값이 256비트(32바이트)이고 이 값을 base64URL으로 인코딩한다. 인코딩 과정에서 base64가 3바이트 단위로 인코딩을 하므로 padding(=)이 붙게 된다.
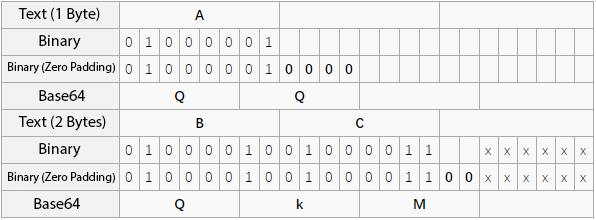
그런데 사실 = 뿐만 아니라 마지막 바이트의 마지막 두 비트까지 00으로 padding이 붙는다. 따라서 디코딩 과정에서 마지막 바이트의 마지막 두 비트는 원본 데이터에 영향을 미치지 못한다.
바꿔 말하면 마지막 바이트의 마지막 두 비트에 00, 01, 10, 11 넷 중 아무거나 들어가도 같은 값으로 디코딩된다. 디코딩 값이 같다면 coupon 값에서 한 비트씩 값을 증가시켜도 서명 검증을 통과하기 때문에 여러번 coupon을 등록하는 것이 가능하다.
JWS의 구현 상 발생하는 문제로 어떻게 써먹을 수 있을진 모르겠지만 다른 곳에서도 사용할 수 있을 것 같다.
0x02. Exploit
Memory Leak
user_db->user_list[32] 이후의 영역(Welcome! 계정)의 메모리는 다음과 같다.
# Welcome!
pw_ptr를 의미하는 영역에는 user_list의 시작 주소인 0x7fffffffdf60가 담겨있고, pw_size를 의미하는 영역에는 계정의 개수를 의미하는 count가 담겨있다.
현재 count는 main() 초반부에 호출되는 setup_admin_7D3A()에서 admin 계정을 추가하면서 1이 되어있다. 따라서 Welcome! 계정의 비밀번호는 0x7fffffffdf60에 저장된 1바이트이다.
이를 이용해 user를 늘려가며 1바이트씩 비밀번호를 brute forcing하여 memory leak이 가능하다.
# admin
0x7fffffffdf60은 다시 말하면 user_list[0]이고 최초의 계정인 admin의 정보가 저장되어있다. count는 최대 32까지 증가시킬 수 있으므로 최대 32바이트까지 leak이 가능하지만, 마지막 8바이트는 basic_string의 기타 데이터이므로 총 26바이트만 leak을 시도했다.
이를 통해 stack 주소와 admin의 pw를 획득할 수 있다.
=
continue
=
+=
break
=
return
\t, \n 등을 의미하는 값들은 입출력상 leak이 불가능하지만 자주 발생하는 문제는 아닌 것 같다.
Win Game
로그인을 하면 Play Game, Apply Coupon, Coupon usage history, Change PW, Print Information중 하나를 할 수 있다.
이 중 Change PW와 Print Information은 Play Game에서 보스를 쓰러뜨리고 regular member가 되어야 사용할 수 있는 메뉴이다.
문제를 풀 때는 다음 단계로 넘어가기 위해 일단 게임을 깼는데 지금처럼 먼저 exploit 시나리오를 세워서 목적을 가지고 진행하는 습관을 들여야겠다.
OOB 취약점을 이용해서 Welcome! 계정으로 게임을 깨고 Change PW를 호출하면 pw_ptr이 가리키는 곳의 값을 변경할 수 있다. Welcome!->pw_ptr은 admin->pw_ptr이 저장된 주소를 가리키고 있으므로, admin->pw_ptr을 원하는 주소로 바꿔놓고 admin으로 로그인해서 다시 Change PW를 호출하면 앞서 설정한 원하는 주소에 데이터를 쓸 수 있는 AAW를 획득할 수 있다.
다만 완전히 AAW는 아닌 것이 admin->pw_ptr을 바꾸는 순간 admin으로 로그인을 하기 위해 필요한 비밀번호가 바뀐다. 따라서 데이터를 쓸 주소에 저장된 값을 알고 있어야 하는데, 지금 생각해보니 Welcome!의 비밀번호를 바꿀 때 admin->pw_size까지 1로 바꿔서 brute forcing을 해도 괜찮을 것 같다.
아무튼 게임은 나를 따라오는 Enemy를 피해 Item을 획득해서 Attack과 Defense를 올린 뒤 Enemy와 싸워야 하는데 Item을 다 먹어도 Enemy를 이길 수 없다.
이 때 가입 시 발급되는 coupon을 이용하면 Attack이 두 배가 되므로 JWT counterfeit 취약점을 이용해 총 네개의 coupon을 이용하면 Enemy를 이길 수 있다.
문제는 상술한 AAW를 얻기 위해 Welcome! 계정이 regular member가 되어야하는데 Welcome! 계정은 가입된 계정이 아니다보니 발급된 coupon이 없다.
__int64 __fastcall
다행히 join_8A4A()을 보면 id가 중복되었는지를 user_list를 count까지만 돌면서 확인하기 때문에 Welcome!이라는 계정을 생성할 수 있다. 또한 login_790E()에서도 id만 맞고 pw가 다를 경우 그냥 다음 루프로 넘어가기 때문에 가입 이후에도 33번째 Welcome! 계정에 로그인이 가능하다.
마지막은 생성한 Welcome! 계정의 coupon을 33번째 Welcome! 계정이 사용할 수 있는가인데 디버거에서 secret key를 확인해 jwt.io에서 내용을 확인한 결과 다음과 같이 userid가 같기 때문에 33번째 Welcome! 계정에서 coupon을 사용할 수 있었다.
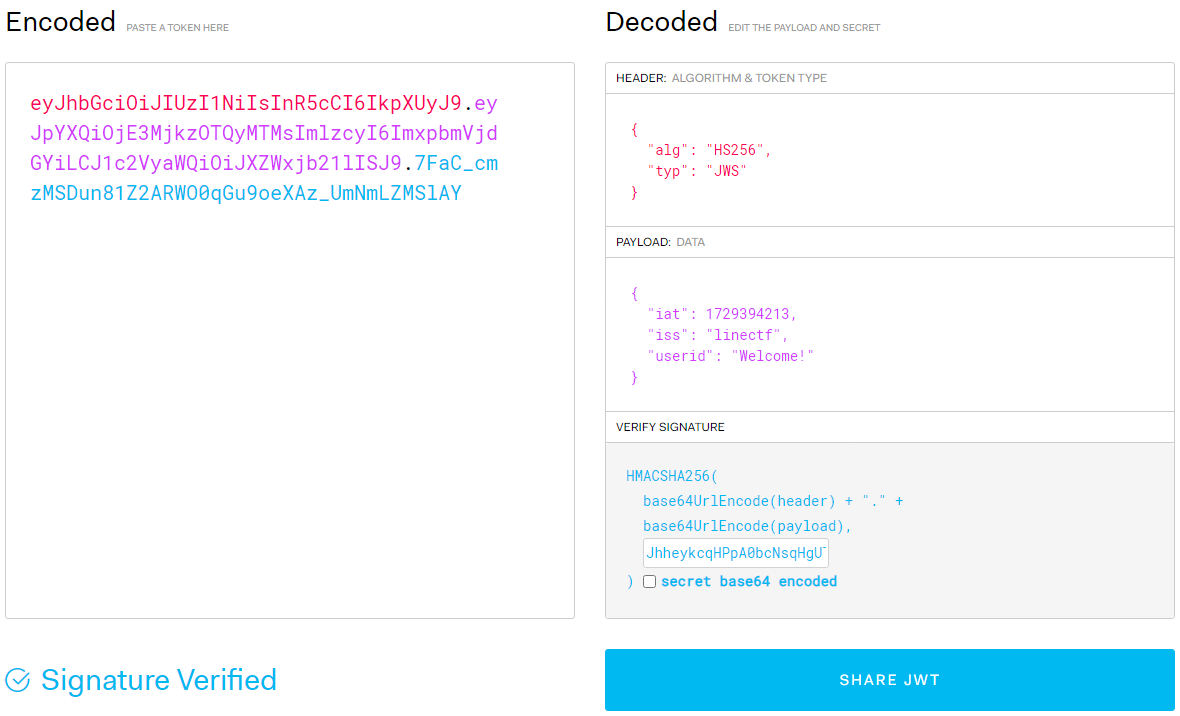
따라서 다음과 같이 payload를 작성했다.
# join fake "Welcome!"
=
=
# counterfeit coupon
이제 게임을 깨야하는데 차후 디버깅을 위해서라도 자동화를 하려고 했는데… 여기에서 ANSI escape code를 사용한 입출력때문에 엄청 오래걸렸다.
결과적으로는 pyte라는 라이브러리를 사용해서 map 정보를 파싱해왔고, Item을 먹는 알고리즘은 좋은게 떠오르지 않아 다음과 같은 단순한 방식을 사용했다.
- 확률을 높이기 위해
Enemy와 한 칸 차이가 되도록 위로 이동 - 맨 왼쪽 아래으로 이동 -
(0, 0) - 맨 왼쪽 위으로 이동 -
(0, 16) Item이 있는 column으로 이동 -(n, 16)- 맨 아래로 이동 -
(n, 0) Item을 다 먹었으면 7번, 남았으면 2번Enemy와 전투
이유는 모르겠는데 (0, 16)에 가면 높은 확률로 Enemy와 두 칸 차이가 나게 되어 Item의 column을 보고 너무 가까운 곳에 있으면 그냥 게임을 재시작하는게 빨라 해당 코드를 추가했다.
Libc Leak
상술한 방법으로 AAW를 얻는다 쳐도 RIP를 어디로 control할 지가 문제이다. 따라서 libc leak이 필요하다고 판단했고, 출력부를 확인해보니 Print Information이 있었다. 여기에서 email을 출력해주는데 email_size가 Welcome!->login_success 영역과 겹친다.
따라서 로그인을 성공시켜 login_success 값을 늘리면 memory leak이 가능할 것으로 판단했다.
주의할 것은 C++이라서 그런지 사용하는 라이브러리가 많아 glibc 영역을 잘 찾아 가져와야한다.
=
=
= - 0x29d90
RIP Control
이제 stack 주소를 알고있으니 main()의 return address를 덮어서 ROP 가젯들을 실행한 뒤 execve를 실행하게끔 payload를 작성했다.
다만 main() 종료 직전에 호출되는 free_db_24FBA()에서 각 user 정보들을 저장한 객체들을 해제하기 때문에 AAW를 위해 바꿔둔 admin->pw_ptr을 원복시켜야 한다.
__int64 __fastcall
따라서 다음과 같이 paylaod를 작성했다.
# change admin->pw to point return address of main
= + 0xd98
# overwrite return address
= + 0x2a3e5
= + 0x2be51
= + 0x904a9
=
+=
+=
+=
+=
+=
+=
+=
# restore admin->pw
0x03. Payload
=
=
=
return
return
return
return
=
return True
return False
return
return
return
=
continue
=
+=
break
=
return
= +
= +
= +
=
return
# 터미널 크기 설정 (24행, 80열 등으로 설정)
=
=
# 화면 출력 파싱 후 'I', 'O', 'E' 위치 찾기
=
continue
return
=
return
=
=
=
# die if too close
= 0
= 1
break
continue
# go to 0, 0
= * 6
+= * 8
+= * 30
=
# farm items
= * 16
+= *
+= * 16
+= *
=
# fight!
return
= 0x555555554000
=
= f
=
=
=
=
=
=
# memory leak using OOB
=
=
=
# join fake "Welcome!"
=
=
# counterfeit coupon
# win game to be regular member
# libc leak by increasing login_success(email_size)
=
=
= - 0x29d90
# change admin->pw to point return address of main
= + 0xd98
# overwrite return address
= + 0x2a3e5
= + 0x2be51
= + 0x904a9
=
+=
+=
+=
+=
+=
+=
+=
# restore admin->pw
# trigger ret in main
=
=